ClearView – Capabilities Defined Info Sheet
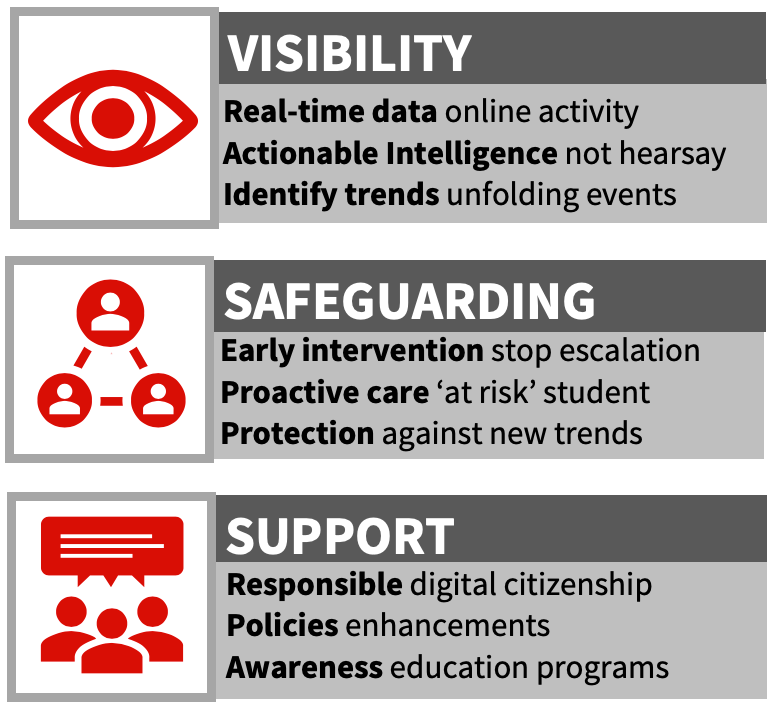
ClearView technology provides detection of behavioural risks including bullying, self-harm and radicalisation. Actionable Intelligence gives schools the ability to see risks for students before they escalate, allowing support to be provided in a timely manner. The unique capability allows analysis of patterns of behaviour and by using evidence-based triggers, design reports and
The ClearView Capabilities Defined document is a guide for understanding how ClearView Behavioural Analytics can be an advantage for student welfare . It demonstrates the flexibility to be pro-active to meet your local environment and develop strategies to address emergence of concerning patterns. Recognise how the data is captured and through CyberHound’s best practice reporting, review data at a summary or detailed level with the ease to drill-down to investigate patterns warranting further investigation.
BEHAVIOURAL ANALYTICS
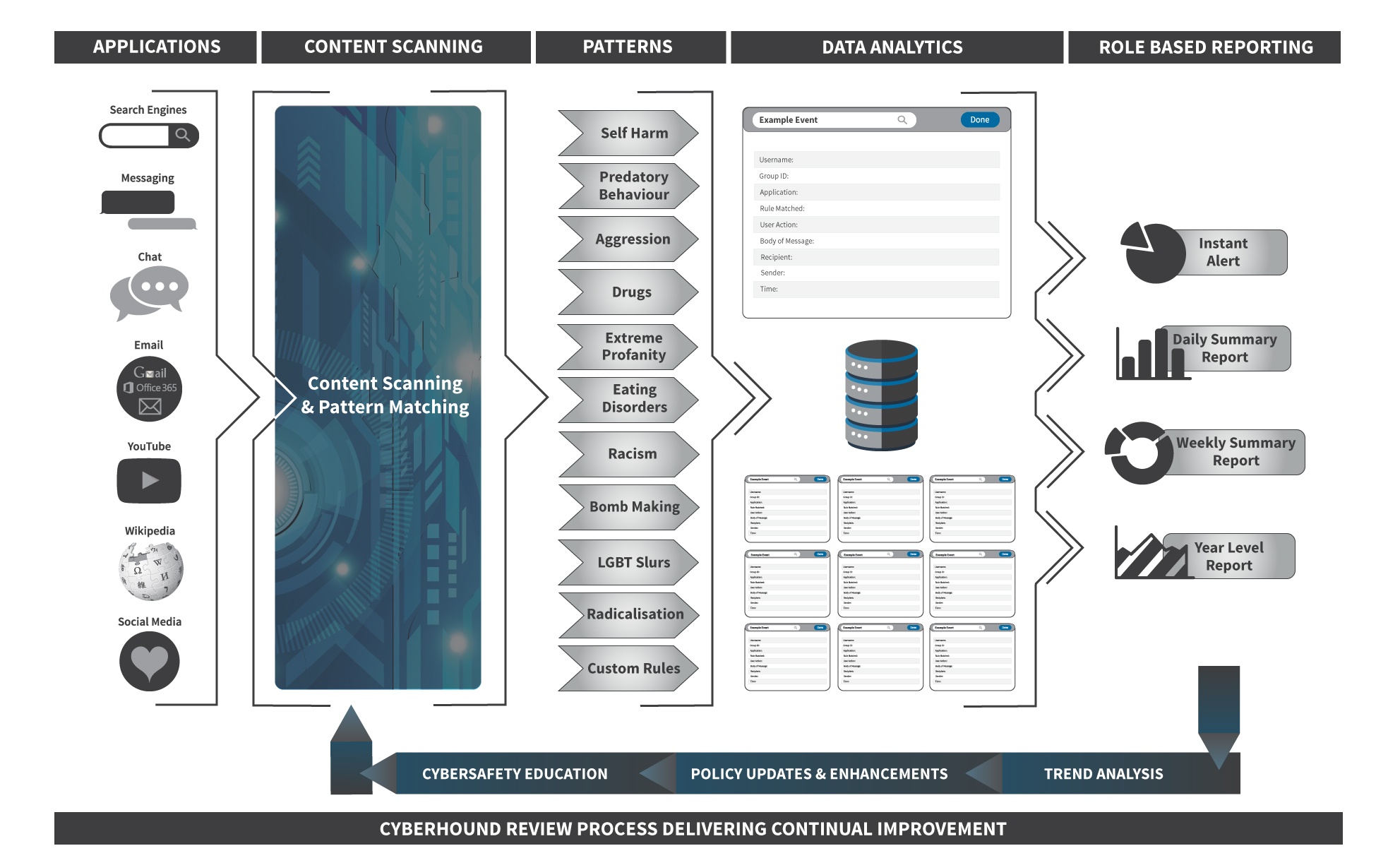
As soon as the ClearView platform is implemented, it automatically identifies patterns of behaviour that indicate a risk or policy breach. It identifies evidence-based triggers that can support the circumstantial events and intuition of professionals within the school.
ClearView provides behavioural analysis via a process of:
- Scanning popular applications.
- Applying Rules and Actions that meet the school policies.
- Scanning content for pattern matching to words or phrases as set by the Rules.
- Collates data for detailed analysis to provide holistic view of the activity.
- Distributes reporting designed specifically for the user and delivered as required.
APPLICATIONS SCANNED

ClearView scans all internet traffic to identify the most common social media, chat, instant messaging and Web 2.0 applications including Facebook, Twitter, Gmail, Yahoo Messenger, MSN, GTalk and Google Hangouts. It also supports popular search engines including Google, Bing, Yahoo, Wikipedia and YouTube. Once a communication stream has been identified it is directed through the ClearView Content Scanning for real-time pattern matching and policy enforcement.
Other application controls are provided by CyberHound’s NextGEN firewall capabilities and are managed by Access Policies.
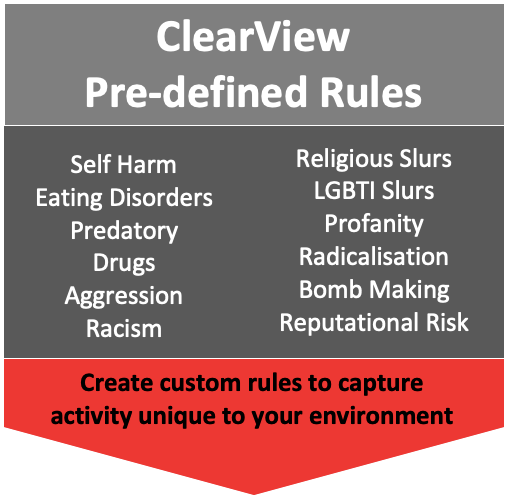
PATTERN MATCHING RULES
There are pre-defined ‘Rules’ available, offering best practice implementations to provide benefits immediately. The patterns are words or phrases that are commonly used for searches or communication.
FLEXIBILITY TO MODIFY THE PATTERN RULE
ClearView provides the flexibility to capture popular expressions; language or trends, specific for your environment. Managing the words or phrases is easily achieved by adding new trends to the relevant pattern-searching rule providing immediate visibility to these new trends or concerning activities or removing unwanted words or phrases that are not relevant for your environment.
EXCLUSIONS
Some
INCLUSIONS
Often there is a need to capture new popular expressions or trends, or words that cause concern. Adding specific words or phrases to the Pattern Matching Rules, will ensure that important trends or concerns can be captured for reporting and provide visibility to the level of interest in these new trends.
Here are some examples that could provide welfare and support staff with evidence-based triggers:
Fights – organised in a nearby park can be monitored easily by adding the name of the park to the Aggression Rule.
Drugs – new slang or street names can be added to the Drugs Rules. Relevant if a local dealer is creating catchy names aimed at students.
Self Harm – trends which may be real or fake, knowing the interest students have in these trends, may assist with re-education programs etc. e.g slender man, momo and blue whale challenge are all examples of recent trends that create news and high levels of curiosity with students.
Reputational Risk – rule is available to add any miscellaneous words or phrases that might not be relevant for an exisiting pattern list. e.g. teachers’ names or nicknames can be added if there are activities surrounding the person, news items that attract unwanted scrutiny could be added for visibility into ‘chatter’ or interest.
Emojis – create a custom Rule to capture inappropriate emojis and have visibility in reports for any that are being used.
Languages – If there are other languages that are prevalent, you can add words or phrases to any of the pattern lists. While those receiving a report with results in another language may not be able to read or interrupt, it will be obvious why it triggered as the ClearView Welfare report is designed to break the data results down to each rule.
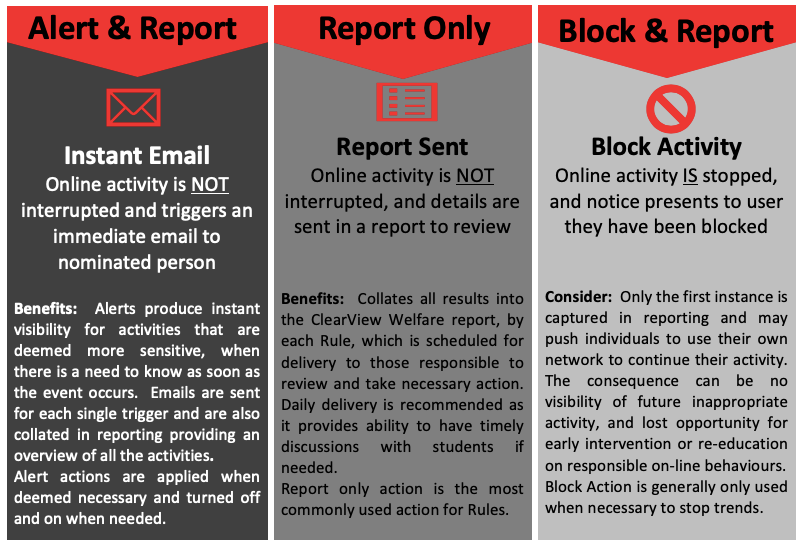
ACTIONS – WHEN RULE TRIGGERS
Actions determine what happens when the words or phrases trigger the rules. The following are actions that are available to apply to any of the ClearView Rules and can be changed when events require a different approach of monitoring.
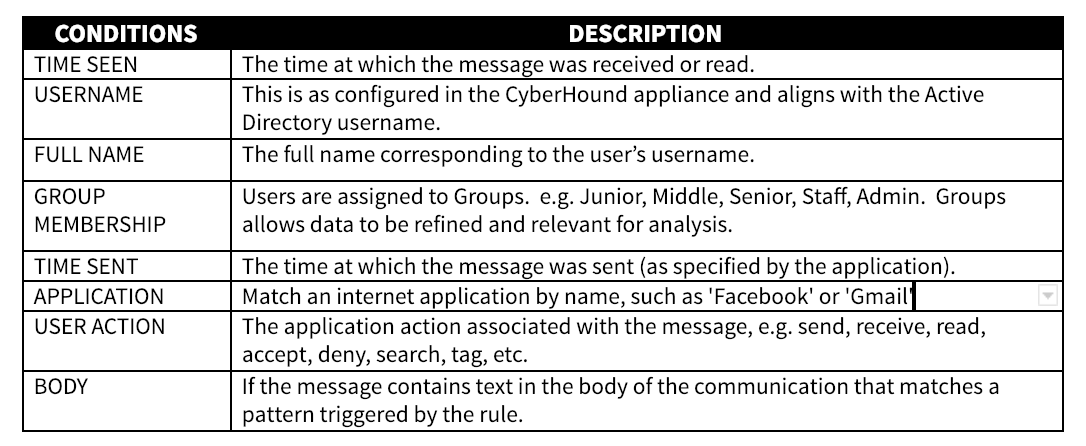
REPORT DATA ANALYSIS CONTEXT
ClearView’s data source captures the results when the patterns are triggered. The data source Query is the tool to analyse results and the ability to drill-down to specific details,
CLEARVIEW WELFARE REPORT
CyberHound provides a ‘best practice’ purpose built set of ClearView queries to define the results and these individual queries are used to build the ClearView Welfare Report.
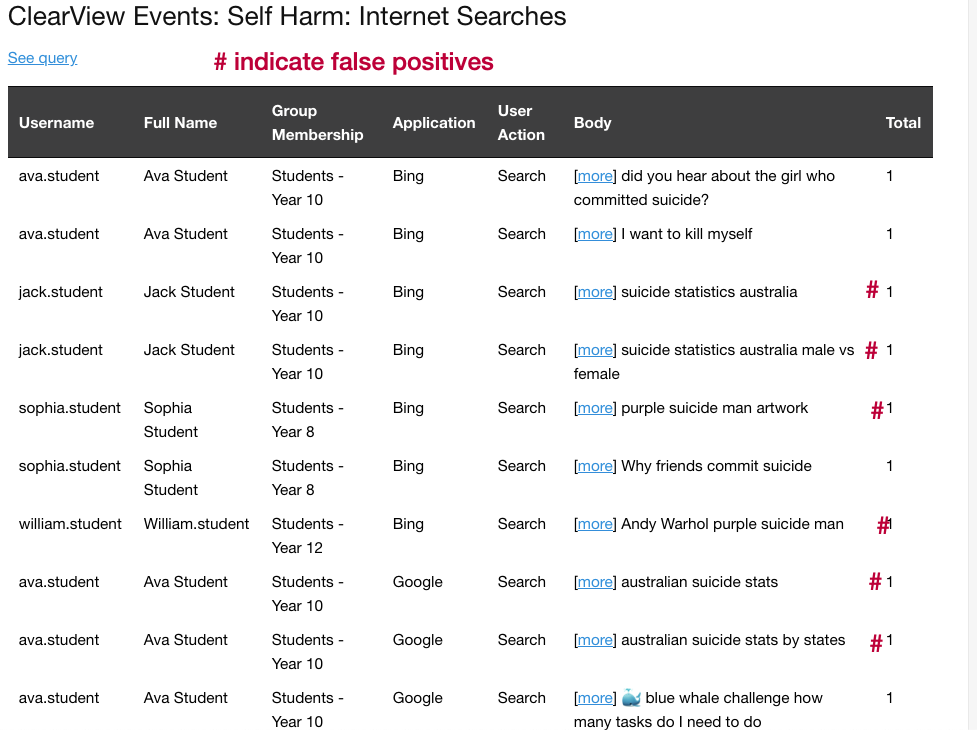
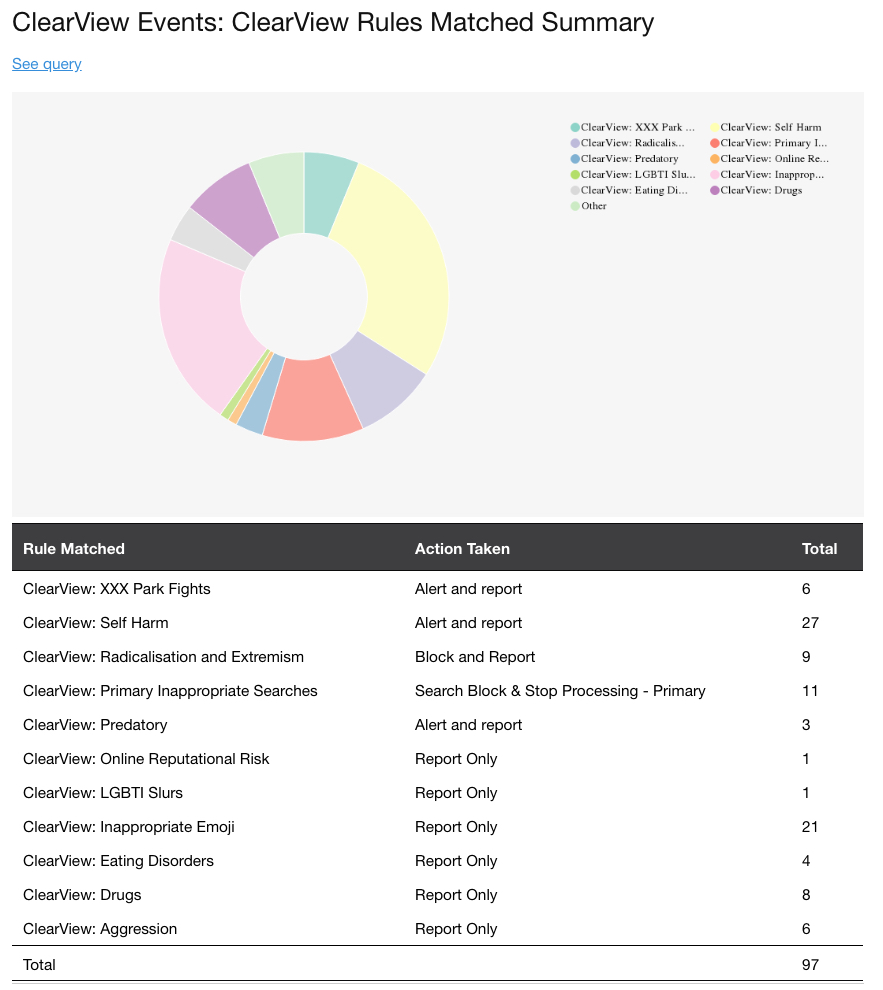
REPORT – SUMMARY CLEARVIEW EVENTS
The summary section provides an overview of each of the Rules matched, and indicates what the current Action is applied to each Rule. Visibility to the Action Taken in daily reports makes it quick to identify when the Action should be changed. e.g. as example below for Radicalisation, perhaps there were some news headlines that you wanted to stop students from searching for a few days, you can assess the activity then request for the Action to be changed back to Report Only.
The summary report totals the event activities against each of the ClearView Rules. Details of the totals are contained within the report with the ability to drill-down to a singular event via the See Query links.
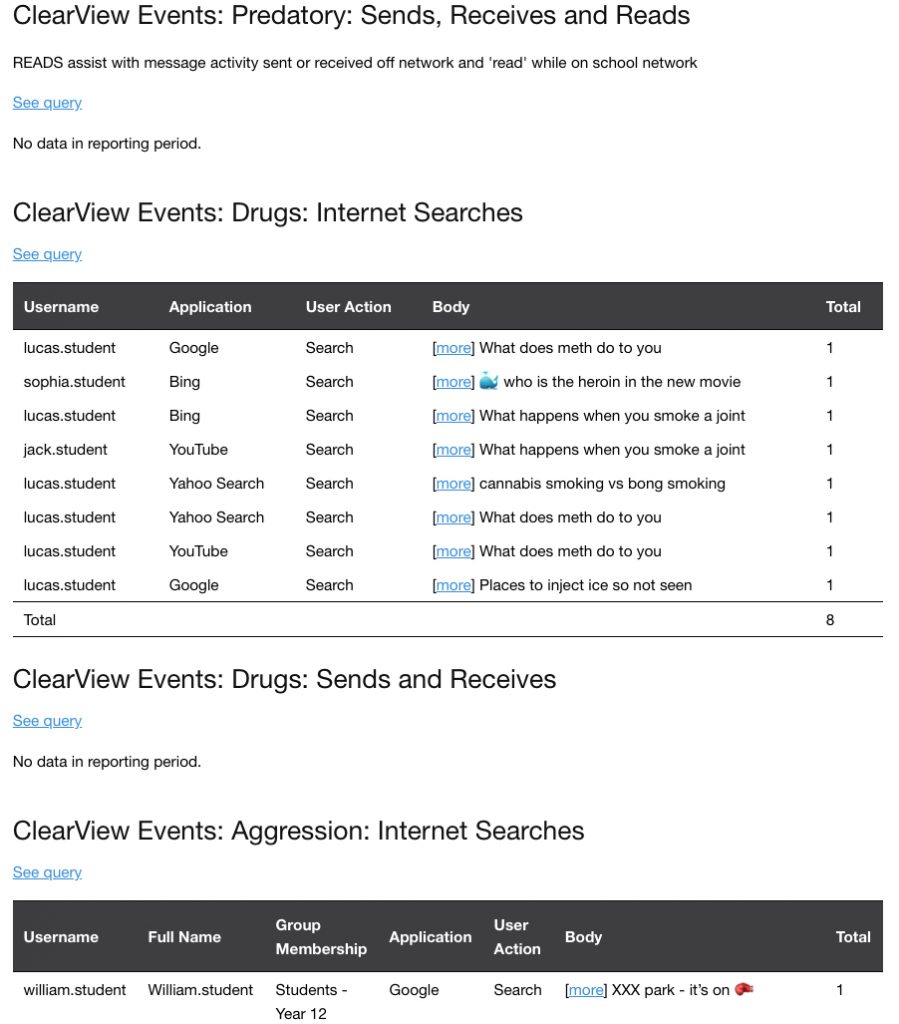
REPORT – DETAILED BEHAVIOURAL ANALYTICS
The detailed section of the report provides specific results for each of the Pattern Rules allowing a scan of activity that may require further investigation. The information for each rule in the report is broken down to outputs that specify the most relevant user activities thus reducing false positives. The report also identifies if there was no results for specified period.
Results for SEARCHES provide insight into a users behaviour and interests which may highlight potential at risk situations.
SENDS or RECEIVES results are combined to provide activity patterns. Who SENT an inappropriate message and who RECEIVED the message, aids in detecting a pattern or commencement of inappropriate behaviour which can be addressed before it escalates. One exception is Predatory were we also include and ‘read’ user activity.
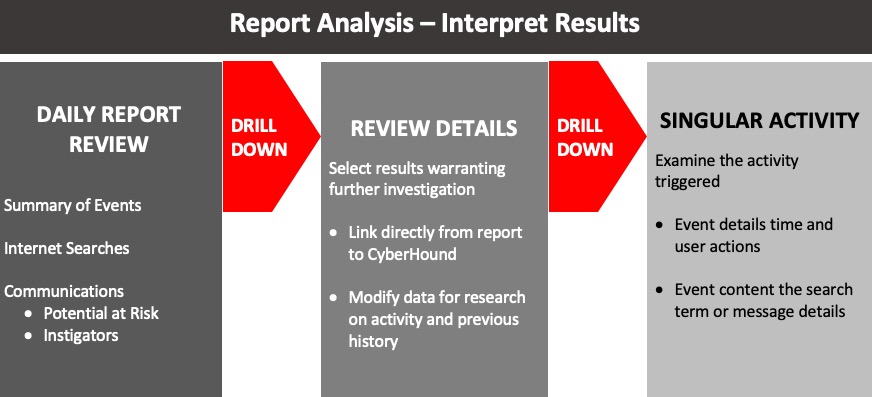
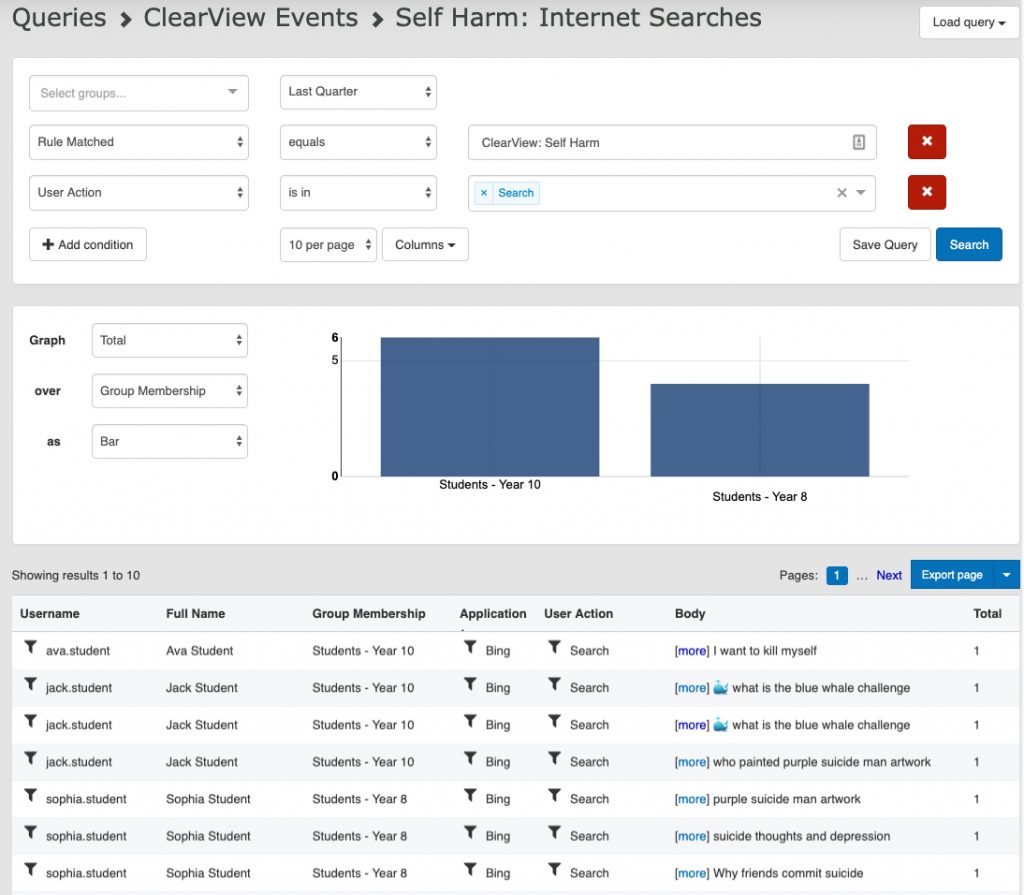
FURTHER INVESTIGATION
Clicking on the ‘See Query’ from the report provides access to CyberHound to view the data source queries for ClearView Events and modify for further investigation of the activity.
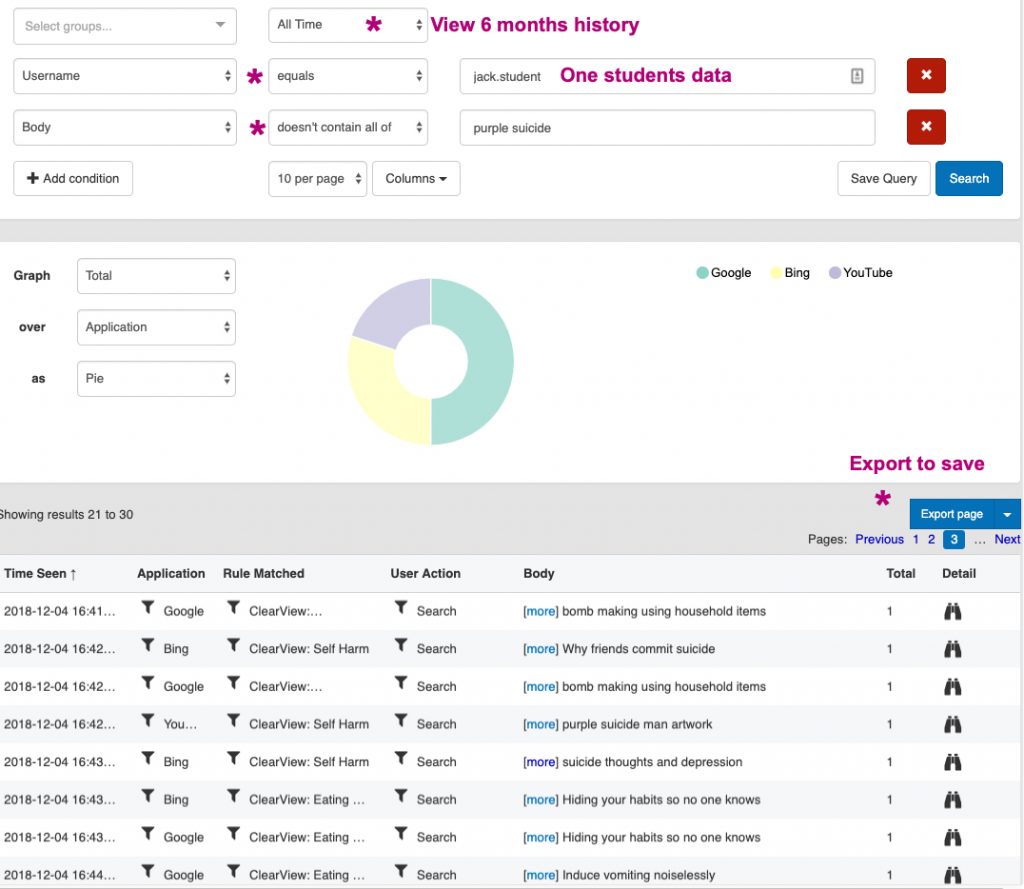
The Query could be modified to search on any parameter e.g. one user over a different period of time or more data results, different headings. Add a condition to exclude the false positives that have not been excluded from the rule as yet e.g. purple suicide.
Exporting the data allows results on specific incidents for future reference be available, as the data source has a maximum records age.
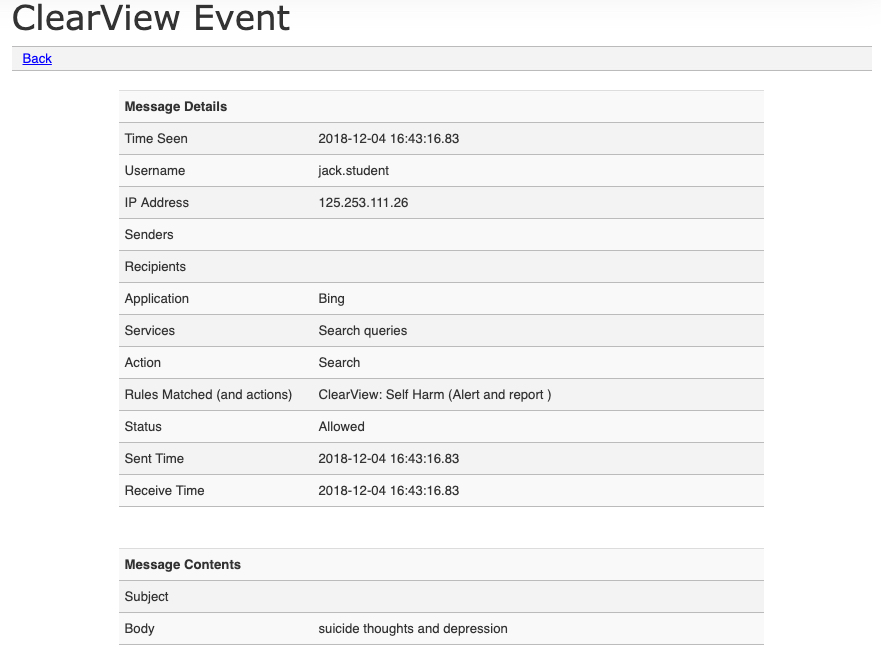
SINGULAR ACTIVITY – MESSAGE DETAILS
Clicking on ‘[More]’ from the results view or the report, provides access to see the details for that singular event. If covers all the message details including the content of the message.